
Symantec (aka Broadcom) provide solutions to help enterprises assure the security, availability, and integrity of their information.

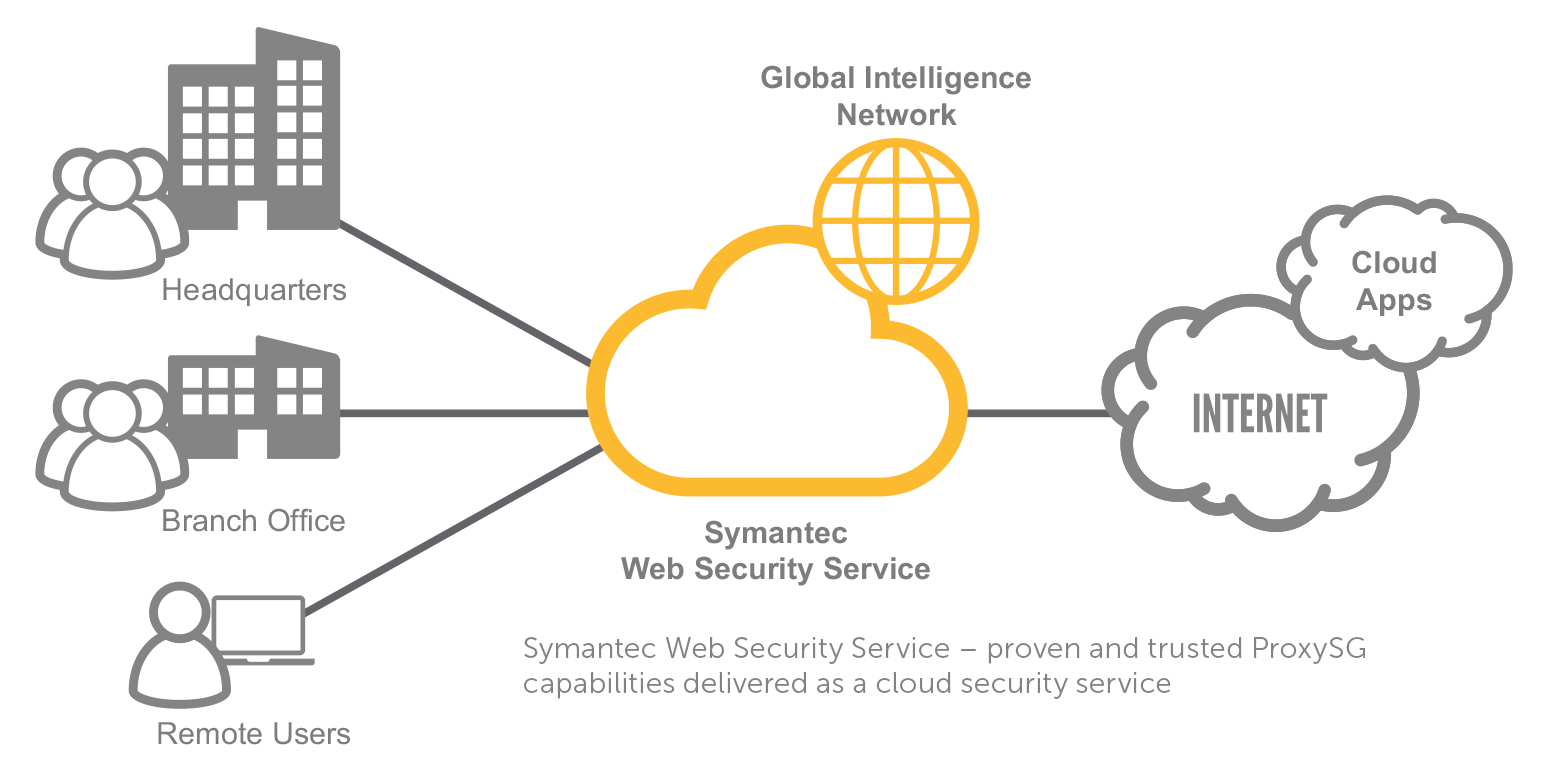
Symantec Web Security Service is a cloud delivered solution that safeguards your staff from Cyber Security risks when using the internet.
Allows user to access web resources and be protected from cyber security risks such as malware, cryptoware, phishing attacks, as well as enforcing policies about how staff are permitted to access the web.
Join us for a Symantec Web Security Service webex demonstration.
Anywhere & Any Device web security.
Comprehensive cloud service to enforce consistent web security and compliance policies for all users, regardless of location or device. Built on an advanced proxy architecture that authenticates every user, to support granular policy delivery, avoiding the need for the users to connect back to the Company network. WSS ships with an agent to achieve seamless authentication to the cloud and apply policy and controls accordingly. Additionally, WSS has inbuilt support SEP or SEP for Mobile to act as the proxy agent, the advantage being single agent simplicity and management. Lastly, for site access, WSS can support your firewall/s or your onsite existing proxy architecture.
The Services are designed to deal with all current and more importantly emerging web threats. This is accomplished by a series of defences that do not depend on one another, rather Symantec accept that no single control should be relied on, and instead offer multiple controls in a series of defensive barriers, this can be thought of as a “Security in-depth” approach, consisting of:
As well as protecting users from internet threats and risks, WSS enforces comprehensive and granular policies about how and when staff can access web resources. Includes a comprehensive list of topics, over 80 web categories and support for over 50 languages to simplify how policy is applied; Syncing with AD to simplify what policies should be applied to user groups. A useful feature is around how a policy should be enforced; there is of course the blunt instrument of blocking access, however there are more subtle options such as:
WSS is global operation to provide the best connectivity access no matter where or how the user access the web, built with multiple and active redundancy capacity to deal with spikes or localized failover offering availability SLA of 99.999%.
A useful consideration for Customers who have adopted other Cloud services is that Symantec are actively creating enhanced connectivity with these providers to reduce latency. Example: Symantec have designed improved links with O365, so that 0365 users accessing a web site via email link experience superior speed.
Opinion & Resources
Symantec WSS is one part of Symantec Network Security portfolio; complementary solutions for WSS include Symantec’s Data Loss Prevention (DLP) solution, which will control how sensitive data is shared and passed through the Web, Endpoint and Email. Symantec's CloudSOC, a CASB (Cloud Access Security Broker) solution to manage access and usage of cloud apps. Lastly, ESS (Email Security Services) is a cloud delivered email security service.
Symantec’s security objective is to secure a business from the three main threat ingress routes: Email, Web and Endpoint. I’m sure you will agree that if you have these three secured, you are in a good shape!
Symantec’s strategy is to deliver these services from the cloud to simplify adoption and reduce resource overheads.